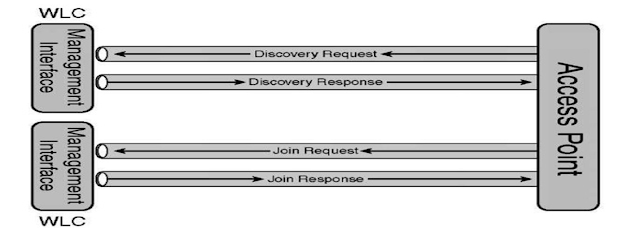
How AP Joins WLC – 1
Debug :
Configuration for DHCP- 43
DNS
After Discovery , Join Request
Join Request
How Controller and AP works
—Light Weight access points cannot act independently .
They are managed by controller .
—2 step Process
—Discover
(Discover the controller)
—Register (Register or join with controller)
How AP Joins WLC – 2
The management interface handles the discovery, whereas
the AP-Manager handles the join.
Note : Some Controller have only one
interface , which acts both as
Management and AP Manager
Type Of Discovery
1.Broadcast
2.Local NVRAM
3.OTAP
4.DHCP Option 43 (Dynamic host configuration Protocol 43)
5.DNS (Domain name system)
1.Layer 2 LWAPP WLC Discovery Algorithm: The LAPs
that support Layer 2 LWAPP mode broadcast a LWAPP discovery request message in
a Layer 2 LWAPP frame, If there is a WLC in the network configured for Layer 2
LWAPP mode, the controller responds with a discovery response . Most of the LAP
and WLC not supporting Layer 2 LWAPP.
2.Layer 3 LWAPP WLC Discovery Algorithm: If layer 2
LWAPP discovery FAILED then LAP uses Layer 3 LWAPP . The Layer 3 LWAPP WLC discovery algorithm is used to
build a controller list. After a controller list is built, the AP selects a WLC
and attempts to join the WLC. The LWAPP Layer 3 WLC discovery algorithm repeats
until at least one WLC is found and joined.
3.Process Involves :
4.After the LAP gets an IP address from the DHCP server,
the LAP begins this discovery process:
5.The LAP broadcasts a Layer 3 LWAPP discovery message
on the local IP subnet. WLC configured for Layer 3 LWAPP mode and is connected
to the same local subnet receives the Layer 3 LWAPP discovery message.
6.Each of the WLCs that receives the LWAPP discovery
message replies with a unicast LWAPP discovery response message to the LAP.
Debug :
For Debugging Layer 2 LWAPP process command used in
controller :
(Cisco Controller) >debug lwapp events enable
Mon May 22 12:00:21 2006: Received LWAPP
DISCOVERY REQUEST from AP 00:0b:85:5b:fb:d0 to ff:ff:ff:ff:ff:ff on port '1' Mon May 22 12:00:21 2006: Successful transmission of LWAPP Discovery-Response to
AP 00:0b:85:5b:fb:d0 on Port 1
For Debugging Layer 3 LWAPP process
command used in controller :
(Cisco Controller) >debug lwapp packet enable
Tue May 23 12:37:50 2006: Start of Packet
Tue May 23 12:37:50 2006: Ethernet Source MAC (LRAD):
00:0B:85:51:5A:E0
Tue May 23 12:37:50 2006: Msg Type :
Tue May 23 12:37:50 2006: DISCOVERY_REQUEST
Tue May 23 12:37:50 2006: Msg Length : 31
Tue May 23 12:37:50 2006: Msg SeqNum : 0
Tue May 23 12:37:50 2006: IE : UNKNOWN IE 58
Tue May 23 12:37:50 2006: IE Length : 1
Tue May 23 12:37:50 2006: Decode routine not
available, Printing Hex Dump
Tue May 23 12:37:50 2006: 00000000: 00
How to identify Discovery type
The value of the IE 58 parameter indicates the discovery type:
1.Broadcast
2.Configured
3.OTAP
4.DHCP server
5.DNS
OTAP - 1
The OTAP feature is disabled by
default . It is applicable for some of the WLC .This is the
discovery process when OTAP is enabled:
1.The LAPs that are already registered to the WLC can
advertise the WLC IP address to the LAPs (in an attempt to find the WLC) with
the use of neighbor messages that are sent over the air.
2.New LAPs that attempt to discover WLCs hear these
messages and then unicast LWAPP discovery request messages to the WLCs.
3.WLCs that receive the LWAPP discovery message reply
with a unicast LWAPP discovery response message to the LAP.
—Debug :
(Cisco Controller) >debug lwapp packet enable
Tue May 23 14:21:55 2006: Start of Packet Tue May 23
14:21:55 2006: Ethernet Source MAC (LRAD): 00:D0:58:AD:AE:CB Tue May 23
14:21:55 2006: Msg Type : Tue May 23 14:21:55 2006: DISCOVERY_REQUEST
Tue May 23 14:21:55 2006: Msg Length : 31
Tue May 23 14:21:55 2006: Msg SeqNum : 0 Tue May
23 14:21:55 2006:
IE : UNKNOWN IE 58 Tue May 23 14:21:55 2006: IE Length : 1
Tue May 23 14:21:55 2006: Decode routine not
available, Printing Hex Dump
Tue May 23 14:21:55 2006: 00000000: 02 .
Tue May 23 14:21:55 2006:
—Note - OTAP was removed from the wireless controller
feature set in code version 6.0.170.0 due to a vulnerability.
NVRAM
If the LAP was registered to a WLC in a previous
deployment, the LAP maintains the list of WLC IP addresses locally in NVRAM. This is the
discovery process:
1.LAPs send a unicast Layer 3 LWAPP discovery request to
each of the WLC IP addresses that the LAP has in its NVRAM.
2.WLCs that receive the LWAPP discovery message reply
with a unicast LWAPP discovery response message to the LAP.
3.Note: If you use the clear ap-config ap_name command in order to reset the LAP to the factory
defaults, all the LAP configurations are reset. The configurations that are
reset include the WLC IP addresses that are stored in NVRAM. In this case, the
LAP must use some other method in order to discover the WLC.
—Debug:
(Cisco Controller) >debug lwapp packet enable
Tue May 23 14:45:36 2006: Start of Packet
Tue May 23 14:45:36 2006: Ethernet Source MAC (LRAD):
00:D0:58:AD:AE:CB
Tue May 23 14:45:36 2006: Msg Type :
Tue May 23 14:45:36 2006: DISCOVERY_REQUEST
Tue May 23 14:45:36 2006: Msg Length : 31
Tue May 23 14:45:36 2006: Msg SeqNum : 0
Tue May 23 14:45:36 2006: IE : UNKNOWN IE 58
Tue May 23 14:45:36 2006: IE Length : 1
Tue May 23 14:45:36 2006: Decode routine not
available, Printing Hex Dump Tue May 23 14:45:36 2006: 00000000: 01 . Tue May 23 14:45:36 2006:
DHCP 43
1.The IP address that should be configured as DHCP
option 43 is the address of the controller Management interface.
2.This is the discovery process:
3.When an LAP gets an IP address from the DHCP server,
the LAP looks for WLC IP addresses in the option 43 field of the DHCP offer.
4.The LAP sends a Layer 3 LWAPP discovery request to
each of the WLCs that are listed in the DHCP option 43.
5.WLCs that receive the LWAPP discovery message reply
with a unicast LWAPP discovery response message to the LAP.
6.Note: You can use DHCP option 43 when the LAPs and the WLCs
are in different subnets.
Configuration for DHCP- 43
—Enter configuration mode at the Cisco IOS CLI.
—Create the DHCP pool, which includes the necessary
parameters, such as the default router and server name.
—This is an example DHCP scope:
ip dhcp pool <pool name>
network <ip network>
<netmask>
default-router
<default-router IP address>
dns-server <dns server IP
address>
Add the Option 43 line with this syntax:
option 43 hex
<hexadecimal string>
The hexadecimal string in step 3 is assembled Like( TLV ) Type + Length
+ Value.
Type = 0xf1(Fixed)
Length = Number of controller management IP addresses times 4 in hex.
Value = IP address of the controller listed sequentially in hex.
—For example, suppose there are two controllers with
management interface IP addresses, 192.168.10.5 and 192.168.10.20. so
—Type : 0xf1.(T) Length : 2 * 4 = 8 = 0x08. (L)
—The IP addresses translate to c0a80a05 (192.168.10.5) and
c0a80a14 (192.168.10.20). When the string is assembled, it yields
f108c0a80a05c0a80a14. The Cisco IOS command that is added to the DHCP scope
—option 43 hex f108c0a80a05c0a80a14
—Debug:
(Cisco Controller) >debug lwapp packet enable
Tue May 23 16:14:32 2006: Start of Packet
Tue May 23 16:14:32 2006: Ethernet Source MAC (LRAD):
00:D0:58:AD:AE:CB
Tue May 23 16:14:32 2006: Msg Type :
Tue May 23 16:14:32 2006: DISCOVERY_REQUEST
Tue May 23 16:14:32 2006: Msg Length : 31
Tue May 23 16:14:32 2006: Msg SeqNum : 0
Tue May 23 16:14:32 2006: IE : UNKNOWN IE 58
Tue May 23 16:14:32 2006: IE Length : 1
Tue May 23 16:14:32 2006: Decode routine not
available, Printing Hex Dump Tue May 23 16:14:32 2006: 00000000: 03 .
Tue May 23 16:14:32 2006:
DNS
You can also use the DNS server in order to return WLC IP
addresses to the LAP. This is the discovery process:
—The LAP attempts to resolve the DNS name
"CISCO-LWAPP-CONTROLLER.localdomain.”
—When the LAP is able to resolve this name to one or more
WLC IP addresses, the LAP sends a unicast Layer 3 LWAPP discovery request to
each of the WLCs.
—The WLCs that receive the LWAPP discovery message reply
with a unicast LWAPP discovery response message to the AP
Note: The AP is informed of this domain name through DHCP option
15. DHCP option 15 specifies the domain name that the AP should use for DNS
resolution. Therefore, it is necessary that DHCP option 15 be configured with
the domain name information in DHCP configuration. This allows
the DHCP server that sends the IP address of the DNS server.
Debug: (Cisco Controller) >debug lwapp packet enable
Tue May 23 16:14:32 2006: Start of Packet Tue May
23 16:14:32 2006: Ethernet Source MAC (LRAD): 00:D0:58:AD:AE:CB
Tue May 23
16:14:32 2006: Msg Type :
Tue May 23 16:14:32 2006: DISCOVERY_REQUEST
Tue May 23 16:14:32 2006: Msg Length : 31
Tue May 23 16:14:32 2006: Msg SeqNum : 0
Tue May 23 16:14:32 2006: IE : UNKNOWN IE 58
Tue May 23 16:14:32 2006: IE Length : 1 Tue May 23
16:14:32 2006: Decode routine not available, Printing Hex Dump Tue May 23
16:14:32 2006: 00000000: 04 .
Tue May 23 16:14:32 2006:
After Discovery , Join Request
LAP selects a WLC from the candidate WLC list and
sends that WLC an LWAPP join request. To join the controller, the access point and controller
perform the following process:
—1. AP sends Join Request
a. Random Session ID
b. X.509
Certificate of LWAPP
—2. Controller
Verification
a. Verifies LWAPP
X.509 Certificate was signed by a trusted CA
b. Generates
random AES encryption key for LWAPP Control traffic
c. Encrypts AES
key using LWAPP Public Key
d. Concatenates key ciphertext with the Session ID
from LWAPP Join Request
e. Encrypts
concatenated string with Controller’s Private Key
—3. Controller
sends Join Response
a. Ciphertext (Session ID,
encrypted AES key)
b. Controller’s
X.509 Certificate
Join Request
—4. LWAPP
Verification
a. Verifies
Controller X.509 Certificate was signed by a trusted CA
b. Decrypts
concatenated string using Controller’s Public Key
c. Validates the
Session ID
d. Decrypts the
AES key using LWAPP’s Private Key
—5. Join Process
is now completed
—6. AES Key
Lifetime timer is 8 hours
a. LWAPP sends
LWAPP Key Update Request (contains new Session ID)
b. Controller
generates new AES key and encrypts as stated above.
c. Controller
sends LWAPP Key Update Response
How Controller and AP works
—Discover and join the controller
—LWAPP message exchange
—AP initiates a firmware download from the WLC (if
there is a version mismatch between the AP and WLC).
—Then, WLC provisions the LAP with the configurations that are
specific to the WLANs so that the LAP can accept client associations.
It includes :
1.Service set identifier (SSID)
2.Security parameters
3.Data rate
4.Radio channels
5.Power levels
CPAWAP vs LWAPP
Light Weight Access Point Protocol (LWAPP) :
Fragmentation/Re-assembly : Relies on IpV4
Path-MTU Discovery: Not supported
Control Channel Encryption between AP and WLC: Yes (using AES)
Data Channel Encryption between AP and WLC: No
UDP Ports: 12222, 12223
Path-MTU Discovery: Not supported
Control Channel Encryption between AP and WLC: Yes (using AES)
Data Channel Encryption between AP and WLC: No
UDP Ports: 12222, 12223
Control And Provisioning of Wireless Access Points(CAPWAP) : It is build on top of LWAPP
Fragmentation/Re-assembly: CAPWAP itself does
both
Path-MTU Discovery: Has a robust P-MTU discovery mechanism, can also detect dynamic MTU changes.
Control Channel Encryption between AP and WLC: Yes (Using DTLS)
Data Channel Encryption between AP and WLC: Yes (using DTLS)
UDP Ports: 5246 (ctrl) 5247 (data)
Path-MTU Discovery: Has a robust P-MTU discovery mechanism, can also detect dynamic MTU changes.
Control Channel Encryption between AP and WLC: Yes (Using DTLS)
Data Channel Encryption between AP and WLC: Yes (using DTLS)
UDP Ports: 5246 (ctrl) 5247 (data)




No comments:
Post a Comment